
The smart plug threat continued
Our research which will explore whether other smart plugs pose the same vulnerabilities as the Sonoff S26, as well as demonstrating how attackers could plant malicious firmware on a smart plug, plant it back into the supply chain, and launch cyber attacks from your WiFi network.
In our last blog we explored the existing vulnerabilities on the Sonoff S26 smart plug, highlighting weak and publicly accessible passwords, unencrypted traffic, and easy to capture WiFi credentials.
This week’s blog is a continuation of our research which will explore whether other smart plugs pose the same vulnerabilities as the Sonoff S26, as well as demonstrating how attackers could plant malicious firmware on a smart plug, plant it back into the supply chain, and launch cyber attacks from your WiFi network. Check out the first part here.
Looking for similarities
Before working on the firmware, we turned our attention to the Ener-J device to see if it had similar vulnerabilities to the Sonoff S26.
The Ener-J device was placed in AP pairing mode according to the supplied instructions which broadcast an SSID, or network name, of SmartLife-xxxx which was not protected by any form of WiFi encryption. It did, however, use message level encryption which prevented the credentials from being intercepted trivially. Although it may be possible to obtain the encryption key from the mobile application or from the device firmware, this was left for a future assessment.
We connected to the WiFi network broadcast by the Ener-J devices and ran a simple port scan to see if there were any services listening like the Sonoff device. We found no TCP ports listening. Again, we used the Wireshark packet sniffer to receive packets and started the pairing process using the mobile application.
Whereas the Sonoff mobile application connected automatically to the device, with the Ener-J we were prompted to manually connect to the SmartLife WiFi network. After doing so, the pairing process was complete.
An interesting observation whilst pairing both devices was that the user is requested to grant permission for location services which seemed unnecessary and overly intrusive.
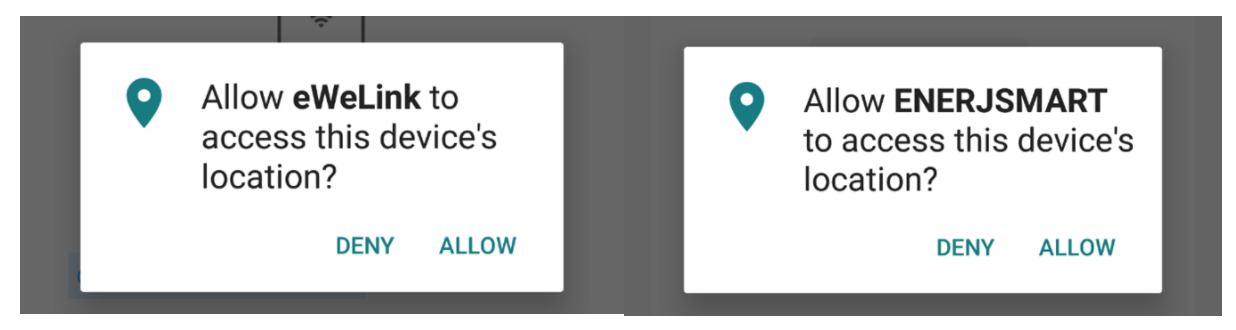

gure 1: Both mobile applications requested permission to retrieve the user’s location
Installing firmware
Our next objective was to see how easily an attacker could alter the firmware on a device at any point post manufacture so we opened up the devices to see how we might replace the stock firmware.
Both the casing on the Sonoff and that of the Ener-J were very easy to disassemble and reassemble without leaving any indication that this had happened.
Having opened the casing on both devices it was a very quick process to identify the brains of the smart plugs and it was clear that creating new firmware to perform our malicious functionality would be a walk in the park.

Both devices used chips from Espressif which were very similar in functionality. The version used by the Sonoff S26 (ESP8266) is popular in both commercial devices and hobby projects so there is a lot of information and tools available online for creating firmware.
The firmware can be downloaded or uploaded (flashed) using four connections between the chip and a USB to serial converter which, like the smart plugs themselves, can be obtained very cheaply.
Given the similarities of the chipset used by the devices, the process for creating and flashing the firmware would be pretty much identical. We decided to concentrate on the Sonoff device as we already understood how it received WiFi credentials and we would want to retrieve these in our new firmware.
Customising the firmware
Now it was time to start writing some code for our custom firmware. At this point the malicious functionality is limited to your imagination whilst keeping the firmware small enough to fit into the available storage of the smart plug.
As a starting point it was decided that the firmware would pair with the mobile application thus retrieving the WiFi credentials, connect to the WiFi network and call home providing the network name (SSID), the pre-shared key (PSK/Password), and the location of the smart plug.
But our smart plug didn’t have GPS so how would we be able to retrieve its location?
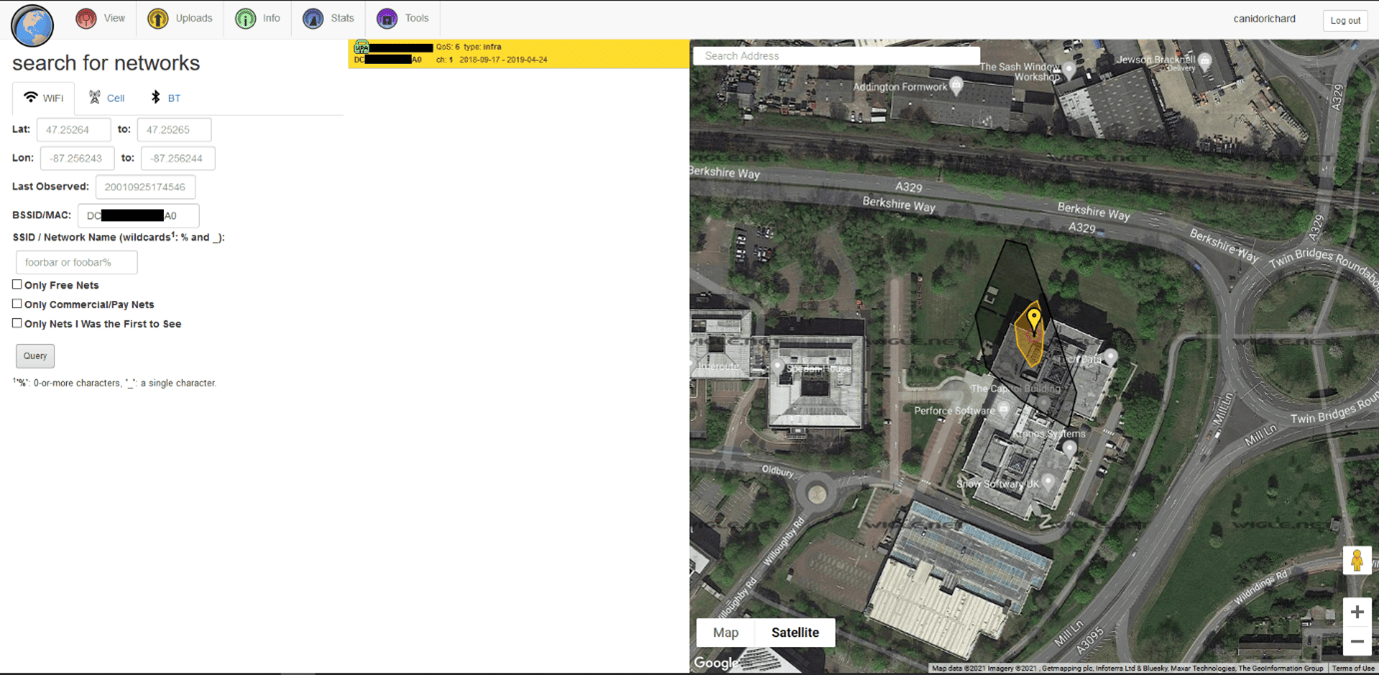
Every access point or WiFi router has a unique base station ID (BSSID) which is broadcast continuously and many of these can be found using the WIGLE WiFi database (wigle.net). We had the firmware scan for the strongest WiFi signal and provide that station’s BSSID when we call home, which could then be used to discover the location. Alternatively, the firmware we installed could have performed the location lookup, but it’s better to minimize the functionality required in the smart plug where possible to reduce firmware size and keep communication to a minimum to avoid detection.
The next step was how to call home, which we did by sending messages using a specially crafted DNS packet. The benefit here is we have a good chance of getting our message through on more restricted networks and the smart plug never makes a direct connection to our servers.
I had already coded a solution for sending and receiving messages over DNS for a previous Red Team engagement (source code has been made available at https://github.com/canidorichard/DNSMsg) so we re-used the server to receive messages from our custom firmware.
A few hours later and we had some malicious firmware ready to flash to the smart plug, which despite being a little rough around the edges met our initial requirements.
It is worth pointing out here that the ESP8266 chip (used in the Sonoff S26) is capable of being updated remotely via over the air (OTA) updates so once our malicious software has been flashed via a cabled connection, we can update with any future firmware versions even if the device is plugged in on the other side of the world. It just needs to be connected to the Internet.
Furthermore, with information such as a network name, PSK, and the location of the smart plug, an attacker would be able to create a database of WiFi networks with credentials and their locations which would be extremely valuable to them as well as being marketable on the dark web.
For the next step, the code was compiled to create a binary firmware image and then flashed to the Sonoff smart plug. After some initial testing, it was then taken to our offices in Bracknell where it was plugged in and setup using the eWeLink mobile application mentioned earlier.
Using the BSSID received from the smart plug we performed a lookup using the Wigle database and as expected were presented with a fairly accurate location – certainly accurate enough for an attacker to make use of the WiFi network for which they now have credentials.
A cheap but serious threat
For our research purposes we created a single smart plug with malicious firmware, but we could just as easily flash the firmware to thousands of smart plugs and place them back in the supply chain to be sold to unknowing consumers. These smart plugs are sold by several suppliers including many on eBay, AliExpress and Amazon. Cyber security criminals could very easily buy thousands of these devices, install malicious firmware, and list them on eBay for a little cheaper than the other suppliers. Every one of them purchased would then provide access to a new WiFi network from which they could launch cyber attacks without the fear of being caught.
Excluding the computer used for developing and flashing the firmware all that is needed is a USB to serial adapter and some connecting wire costing less than £5.
With the popularity and low cost of smart plugs, it’s likely that further brands are either unsecure on purchase or can be easily tampered with by malicious actors and reintroduced to the supply chain. As such, both manufacturers and consumers need to be aware of the risks and know what steps they can take to reduce the likelihood of attack through these cheap smart plugs.
The onus certainly falls on the manufacturer to take any tamper proofing measures, examples of which include:
Glue or weld plastic enclosures so that it is more difficult to tamper with a device without leaving evidence in the form of cosmetic damage to the enclosure.
- Use hardware that requires a cryptographically signed firmware image.
- Coat components and connections required for dumping/flashing firmware with an epoxy resin, the removal of which would damage the components leaving the device inoperable.
- Use only approved distributors to form a trusted supply chain.
- Work with a security consultancy during product design to help ensure devices are as secure as possible before reaching production.
But what is it users can do to protect themselves?
- Before doing anything, especially connecting to the network, examine the device for any signs that it has been tampered with.
- Make sure that any smart device would not cause a serious issue if an attacker were to turn them on unexpectedly, for example kettle and heaters could be a fire risk.
- Make sure other devices on the network have any available security patches applied and that laptops/desktops are running up-to-date end point protection software.
- If possible, always place untrusted devices on a separate network. This can be accomplished by connecting a second access point to your internet router creating a separate WiFi network.
- For the more technically savvy, monitor the communications of the device with a packet sniffer and try to confirm that all connections are valid. An organisation may wish to have a vulnerability assessment completed by experienced security consultants.




